Did you know that a staggering number of data breaches originate from vulnerabilities within third-party services? In today’s digital landscape, more and more businesses are relying on Software as a Service (SaaS) applications for everything from customer relationship management to project management and data storage.
This shift offers incredible flexibility and scalability, but it also introduces a whole new set of data security challenges. SaaS data security, in essence, refers to the measures taken to protect sensitive information stored and processed within these cloud-based applications.
But with data residing outside your direct control, are you truly confident in its safety? This article dives deep into the critical aspects of SaaS data security, exploring common risks, best practices, and actionable strategies you can implement to safeguard your valuable information and maintain customer trust.
Prepare to gain a comprehensive understanding of how to navigate the complexities of SaaS security and build a robust defense against potential threats.
SaaS Data Security: Protecting Your Information in the Cloud
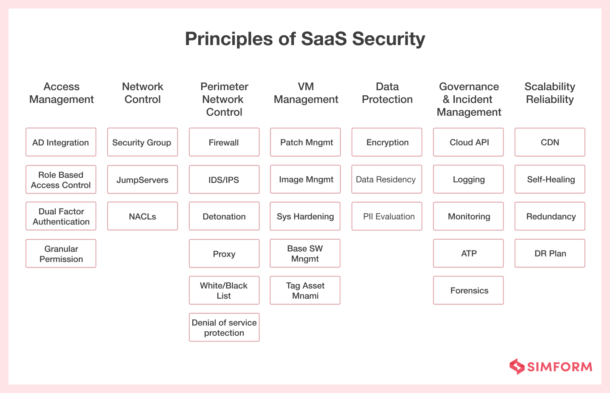
Software as a Service (SaaS) has become an integral part of modern business. It offers flexibility and scalability but also brings significant data security responsibilities.
Understanding the nuances of safeguarding your information in a shared environment is paramount. Proper security measures will protect your organization and customers.
This article will explore key aspects of SaaS data protection, covering best practices. Let’s learn how to mitigate risks and establish a secure SaaS ecosystem.
Let’s dive into the essential elements of robust SaaS data safety!
Understanding the Shared Responsibility Model
The shared responsibility model is a central concept in SaaS security. It clarifies the roles of the SaaS provider and the customer in protecting data.
The SaaS provider manages the infrastructure’s security. This includes physical security, network security, and platform security.
The customer, however, retains the responsibility for data security within the application. This involves managing access controls, configuring security settings, and protecting user accounts.
Customers must understand what they need to be responsible for. This awareness is important to make informed decisions about security investments.
A clear understanding of the shared responsibility model is crucial for effectively managing risk. Failing to understand this divide can leave data exposed.
Key SaaS Data Security Threats
SaaS environments face unique threat vectors. Understanding these common dangers is a vital first step in defense.
Data breaches are a primary concern. They can result from weak passwords, phishing attacks, or vulnerabilities in the SaaS application itself.
Insider threats can also pose a risk. Disgruntled employees or negligent users could inadvertently or intentionally compromise sensitive data.
Additionally, regulatory compliance requirements, such as GDPR or HIPAA, necessitate proper data handling. Failure to comply can lead to legal penalties.
Poor access management increases risks as well. Overly permissive roles or inadequate authentication procedures provide an entry point for malicious actors.
Keeping on top of the newest threats is important, too. Stay vigilant and adapt your strategy.
Implementing Strong Access Controls
Robust access control mechanisms are essential for limiting unauthorized data access. Implement multi-factor authentication for all user accounts.
Adopt the principle of least privilege, granting users only the access they require to perform their duties. Regularly review and update user permissions.
Implement role-based access control (RBAC) to streamline permission management. Define specific roles with predefined access rights.
Employ strong password policies, requiring complex passwords and regular password changes. Monitor user activity for suspicious behavior.
Combine different approaches, such as MFA, RBAC, and strong passwords, for the best results. This approach strengthens the defenses.
Data Encryption: Protecting Data at Rest and in Transit
Encryption is critical for protecting data both when it’s stored and while it’s being transmitted. Encrypt sensitive data at rest using robust encryption algorithms.
Ensure that data in transit is protected using TLS/SSL encryption. Use HTTPS for all web traffic to and from the SaaS application.
Manage encryption keys securely, using a key management system (KMS). Regularly rotate encryption keys to enhance security.
Verify that your SaaS provider supports encryption and allows you to manage your own encryption keys (BYOK – Bring Your Own Key).
Encryption adds a vital layer of defense against unauthorized access. Even if data is intercepted, it remains unreadable without the key.
Regular Security Audits and Penetration Testing
Conduct regular security audits to assess the effectiveness of your security controls. Identify vulnerabilities and weaknesses in your SaaS environment.
Engage a qualified third-party to perform penetration testing. This simulated attack helps to uncover security flaws that could be exploited.
Review your SaaS provider’s security certifications, such as SOC 2 or ISO 27001. This provides assurance that the provider meets industry standards.
Analyze audit logs and security reports regularly to identify potential security incidents. Implement a process for responding to security incidents promptly.
Audits and penetration tests are important checks to find problems. Then these problems can be corrected quickly.
Data Loss Prevention (DLP) Strategies
Data Loss Prevention (DLP) tools and strategies help prevent sensitive data from leaving the organization’s control. Implement DLP policies to identify and block the transfer of sensitive information.
Monitor user activity for suspicious data exfiltration attempts. Use DLP solutions to track and control data movement within the SaaS application.
Educate users about DLP policies and the importance of protecting sensitive data. Train employees to recognize and avoid phishing attacks.
Classify data based on its sensitivity and apply appropriate DLP controls. Implement DLP rules to prevent data from being copied, printed, or emailed without authorization.
DLP protects from accidental data leaks. This adds another layer of defense beyond access controls.